WRONG!!
In fact, in the light of my arguments below, I might even boldly describe the entire debate as ‘Rubbish’. But before I launch into another one of my inescapable arguments, let’s have a quick look at some of the pros and cons of IT as an outsourced service and as an internal function. Since this blog is primarily dedicated to small business IT, we won’t even talk about the hybrid combination model. The very idea of hiring an IT staff and then outsourcing that function can only make sense (I guess) in a large organisation.
| External (Outsourced) IT Pros
Cons
| Internal IT Pros
Cons
|
- Google Apps for Work or Office365 for emails
- Salesforce or Insightly for CRM
- Dropbox, Google Drive, OneDrive or a NAS drive for files
- Cloud-based services for other applications and
- Has BYOD or COPE framework deployed
Pros of External (Outsourced) IT
- With no expensive and eternally outdated hardware such as servers to maintain, the cost of outsourced IT function can become an unjustified expense
- Small business IT requirements are generally uncomplicated. Cloud-based services come with plenty of technical support and can work independently of other services. This eliminates the need to retain specialised expertise.
- SLAs for outsourced IT support are complicated and often come with lock-in contracts that can be very expensive to get out of. Cloud-based services do offer SLAs but usually don’t have long term contracts.
Cons of Internal IT
- The simplicity and ease-of-use of cloud-based systems do not always require a dedicated technical staff maintaining them. Moderate technical acumen within operations staff will more than suffice.
- With cloud services you have access to the expertise of wide range of IT specialists providing cutting edge technology at extremely affordable prices.
- Although far less frequent, cloud systems do have outages but the good thing about those times is the knowledge that there is nothing your staff can do and that some of the best engineers would be working tirelessly to get it back up and running without any excuses and overtime pay.
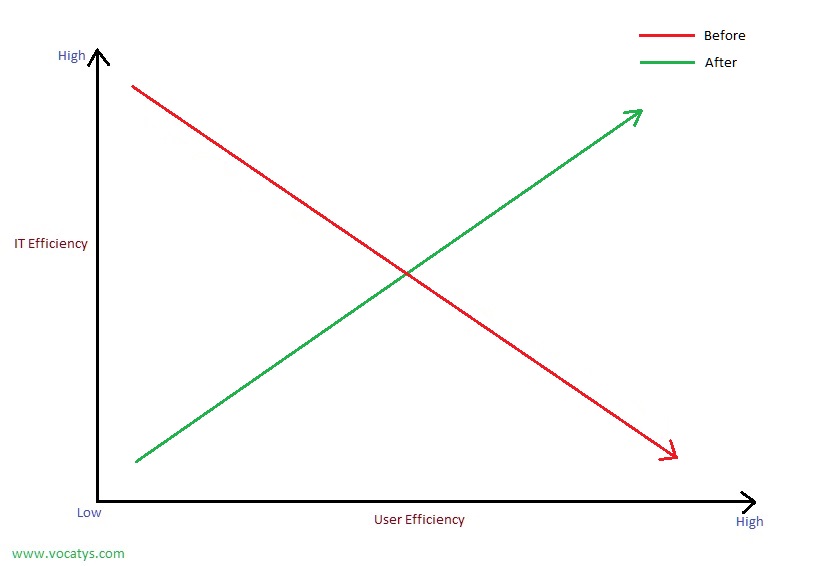
As far as the IT needs of any business is concerned, internal IT function has always been the first choice. Cost is the only primary reason why it is outsourced. Emerging cloud and mobile technologies are, however, radically changing this. You now, not just get better for less but amazing for a fraction and still don’t need an IT whiz-kid to manage it all.
This article was written by Austin D'Mello, Managing Partner of Vocatys, an emerging technology consulting company. If you liked this article please share it with your network. You can also subscribe to the monthly Vocatys newsletter by emailing us at [email protected].








 RSS Feed
RSS Feed